- Wps Pin For Laptop
- Jumpstart Wps Pin Locked Lock
- Jumpstart Wps Pin
- Download Jumpstart Wps
- Jumpstart Wps Pin Locked Reset
JumpStart - Software yang memungkinkan kamu untuk hack wifi yang memakai keamanan WPS. Dijamin ampuh dan bisa terhubung. Cara penggunaan software ini mudah, kamu bisa terhubung dengan wifi yang diinginkan hanya dalam beberapa menit. The problem is that after trying some WPS-PINs, the AP lock the WPS so I reaver is not usefull. To solve this, I perform a mdk3 attack to force the AP to reboot and be able to attack it again (after reboot, the WPS restarts in unlocked state).
[YB]This article is an excerpt from my WiFi Penetration testing andSecurity eBook for aspiring WiFi hackers and Wireless security enthusiasts. Click here to learn more[/YB]
In previous chapters we covered:
Today we will learn WPS cracking using reaver.
What is WPS ?
WPS stands for Wi-Fi Protected Setup and was designed to make setting a secure AP simpler for the average homeowner. First introduced in 2006, by 2011 it was discovered that it had a serious design flaw. The WPS PIN could be brute-forced rather simply using tools like Reaver.
What is Reaver ?
Reaver is a free, open-source WPS cracking tool which exploits a security hole in wireless routers and can crack WPS-Enabled router’s current password with relative ease. It comes pre-installed in Kali Linux and can be installed on other Linux distros via source code. Reaver performs a brute force attack against an access point’s WiFi Protected Setup pin number. Once the WPS pin is found, the WPA PSK can be recovered
[YB]Checkout my new store for Best WiFi adapters for Hacking, Best-selling Pentesting Books and Best WiFi Boosters: Rootsh3ll rStore[/YB]
Wps Pin For Laptop
Description:
Reaver-wps targets the external registrar functionality mandated by the WiFi Protected Setup specification. Access points will provide authenticated registrars with their current wireless configuration (including the WPA PSK), and also accept a new configuration from the registrar.
In order to authenticate as a registrar, the registrar must prove its knowledge of the AP’s 8-digit pin number. Registrars may authenticate themselves to an AP at any time without any user interaction. Because the WPS protocol is conducted over EAP, the registrar need only be associated with the AP and does not need any prior knowledge of the wireless encryption or configuration.
Reaver-wps performs a brute force attack against the AP, attempting every possible combination in order to guess the AP’s 8 digit pin number. Since the pin numbers are all numeric, there are 10^8 (100,000,000-1 = 99,999,999) possible values for any given pin number, considering 00,000,000 is not the key. However, because the last digit of the pin is a checksum value which can be calculated based on the previous 7 digits, that key space is reduced to 10^7 (10,000,000-1 = 9,999,999) possible values, again as checksum of first 6 zero’s will be zero, we remove 0,000,000 to be brute-forced.
The key space is reduced even further due to the fact that the WPS authentication protocol cuts the pin in half and validates each half individually. That means that there are (10^4 )-1 i.e 9,999 possible values for the first half of the pin and (10^3)-1 i.e 999 possible values for the second half of the pin, with the last digit of the pin being a checksum.
Reaver-wps brute forces the first half of the pin and then the second half of the pin, meaning that the entire key space for the WPS pin number can be exhausted in 10,999 attempts. The speed at which Reaver can test pin numbers is entirely limited by the speed at which the AP can process WPS requests. Some APs are fast enough that one pin can be tested every second; others are slower and only allow one pin every ten seconds. Statistically, it will only take half of that time in order to guess the correct pin number.
Installing Reaver from Source Code:
System: Ubuntu
Open terminal and type:
If you’ve read previous tutorial, You will know that first we have to put our wireless card on monitor mode and then start scanning.
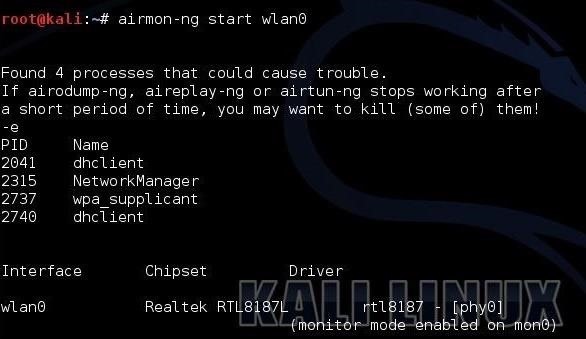
Step 1: Putting Card on Monitor Mode
First kill the programs that may cause issues, then we will put our card into monitor mode.
sudo airmon-ng check killsudo airmon-ng start wlan1
wlan1 is the wireless interface in my case, you can check yours by simply typing in terminal.
iwconfig
Step 2: Scanning the Air for WPS Networks
Airodump-ng has a limitation, It canno detect WPS enabled routers. So, for that purpose we use wash command which installs along with Reaver and helps us scanning for WPS enabled routers.
Just write:
sudo wash -i wlan1mon
It will show a similar output:
Note the “WPS Locked” column; this is far from a definitive indicator, but in general, you’ll find that APs which are listed as unlocked are much more likely to be susceptible to brute forcing. You can still attempt to launch an attack against a network which is WPS locked, but the chances of success aren’t very good.
Here,
ESSID/Target: belkin.ffd
BSSID: EC:1A:59:43:3F:FD
Channel: 11
WPS Locked: Yes
Ms office 2019 free download for windows 7. In case you’re getting an output like this:
Just add “-C” or “–ignore-fcs” with the previous command to skip
- wash -i wlan1mon -C
- wash -i wlan1mon –ignore-fcs
Both will work the same, and ignore FCS packets and you will get previously shown output.
Step 3: Fire up Reaver
After getting the target Ap’s BSSID, we will tell Reaver to try WPS pin attack on that specific BSSID only
- reaver -i wlan1mon -b EC:1A:59:43:3F:FD
In some case, BSSID may be cloaked, or duplicated by another attacker. In that case Rever won’t be able to successfully conduct WPS pin attack. You’ll have to be more precise by providing ESSID and channel number, we earlier noted to Reaver.
- reaver -i wlan1mon -b EC:1A:59:43:3F:FD -c 11 -e “belkin.ffd”
ESSID may contain spaces, so always include ESSID in quotes.
Step 4: Cracking WPS
This part is actually done by Reaver itself, as we’ve already provided necessary information to Reaver. If the router is vulnerable to WPS Pin attack, it will show you an output like this:
If Reaver succeeds in Trying one pin after another, WPS pin and corresponding WPA2-PSK key is most like to be broken in couple of hours (3-5).
It is quite funny that WPS was supposed to provide ease and security to the Homeusers, but a vulnerable WPS enabled router allows a potential attacker to break the security with ease. Not only the WPS key, but also the WPA2 PreShared Key that is considerably a lot hard to crack without WPS.
The Ugly Truth about WPS [For Pentesters]
It’s important to note that new APs no longer have this vulnerability. This attack will only work on APs sold during that 2006 and early 2012. Since many families keep their APs for many years, there are still many of these vulnerable ones around. So once in a while this technique can be useful.
Supported Wireless Drivers
The following wireless drivers have been tested or reported to work successfully with Reaver-wps:
- ath9k
- rtl8187
- carl19170
- ipw2000
- rt2800pci
- rt73usb
Partially Supported
The following wireless drivers have had mixed success, and may or may not work depending on your wireless card (i.e., if you are having problems with these drivers/cards, consider trying a new card before submitting a trouble ticket):
- ath5k
- iwlagn
- rtl2800usb
- b43
Not Supported
The following wireless drivers/cards have been tested or reported to not work properly with Reaver:
- iwl4965
- RT3070L
- Netgear WG111v3
Countermeasures
- Turn off the WPS by the WPS push button, if vulnerable.
- Do not use WPS, if your router is vulnerable and use a strong WPA2 passphrase.
- Check whether your router is manufactured after 2012, It may not be vulnerable.
Useful Links:
Router:
Jumpstart Wps Pin Locked Lock
TP-LINK TL-MR3420 300 MB/s Wireless Router 2x 5dBi antennas (Patched WPS Supported router)
Network Adapters:
Alfa AWUSO36NH High Gain B/G/N USB / Alfa AWUS036NHA B/G/N USB
High Gain Antenna:
USB Drive (32 GB):
SanDisk Ultra Fit USB 3.0 32GB Pen Drive (International)
Jumpstart Wps Pin
SanDisk Ultra USB 3.0 32 GB Pen Drive (India Only)
Download Jumpstart Wps
Did you liked this post ? Do let me know in the comments down below.
Jumpstart Wps Pin Locked Reset
Thank you!

